On Demand Strategic Intelligence Analysis
Strategic Intelligence Analysis - Estimative and Warning Intelligence - 10 Weeks - Intense and Rewarding
- Course
- By Jeff Bardin

Advanced Topics in Cyber Intelligence
From adversary cyber warfare methods to building your intel program
- Bundle

Adversary Targeting
Create models on your adversary - their capabilities, intent, and motivations.
- Course
- By Jeff Bardin
Building a Cyber Intelligence Program - Part 1
This is the part 1 instruction lays out the roadmap for a mature cyber intelligence program
- Course
- By Treadstone 71

Building a Cyber Intelligence Program - Part 4
An in depth look at the different types of analysis and how they work in intelligence analysis.
- Course
- By Treadstone 71

Building a Cyber Intelligence Program - Parts 2 & 3
This section covers the functions and capabilities for an essentional cyber intelligence program.
- Course
- By Treadstone 71
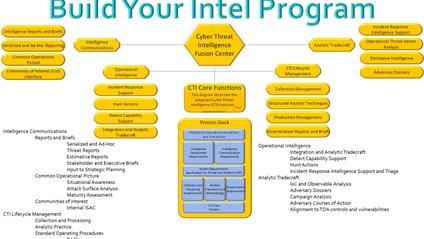
Building and Enhancing Your CTI Program with Strategic Intelligence Analysis - The Formula!
Build and Enhance Your CTI Program - Intensive and In-depth Hands-on - 10 Additional Lectures with Templates and Examples - Learn and Build at the same time
- Course
- By Treadstone 71

Certified Cyber CounterIntelligence Analyst - In Person Course
- Course
- By Treadstone 71

Certified Cyber Intelligence Analyst - In Person Course
- Course
- By Treadstone 71

Chinese Cognitive and Information Warfare Section 1 - Cyber Psyops - APT Groups
Cognitive and Information Warfare tactics, techniques, and methods from the Chinese Perspective
- Course
- By Treadstone 71

Cialdini's Principles
Cyber Cognitive Warfighter
- Course
- By Treadstone 71
Cognitive Warfare Definitions Part 1
Cognitive Warfare Some definitions and concepts - Cyber Psyops
- Course
- By Treadstone 71

Collection Management
Using your knowledge of stakeholders, adversaries, and intelligence requirements, create a collection plan and manage it!
- Course
- By Jeff Bardin

Color Revolutions - Cognitive Warfare - Cyber Psyops
What are color revolutions and what role does cyber cognitive warfare play in them.
- Course
- By Treadstone 71
Conspiracy Theories
Weaponizing Theories to Divide
- Course
- By Treadstone 71

Course Instructor Support - Free to Enrolled Students with a validated email account only.
- Coaching
- By Jeff Bardin
Critical Thinking and Cognitive Bias for Cyber Intelligence
The building blocks of intelligence analysis and the pitfalls you may encounter
- Course
- By Jeff Bardin

Cryptocurrency Certified Cyber CounterIntelligence Analyst - AI-Infused
Cryptocurrency Certified Cyber CounterIntelligence Analyst - AI-Infused. Counter Disinformation, Misinformation while building Cyber CounterIntelligence Plans to Subvert the Adversary
- Course
- By Treadstone 71

Cyber CoIntelPro
Applying Cyber to the FBI Counterintelligence Program - Cointelpro - Cyber Psyops
- Course
- By Treadstone 71

Cyber Cognitive Warfighter Training - Cyber Leadership Combo Course
- Course
- By Treadstone 71

Cyber CounterIntelligence, Disinformation, Cyber Warfare, and Psyops Bundle
Normally well over $5k! Signup now!
- Bundle

Cyber Intel - CounterIntel Bundle
Cyber Intelligence + Counterintelligence Bundle Certified Cyber Intelligence Analyst + Certified Cyber Counterintelligence Analyst (On-Demand) Get Two Flagship Courses. One Bundle. Full-Spectrum Intelligence Tradecraft.
- Bundle

Cyber Intelligence Recertification
Cyber Intelligence Tradecraft, Certified Cyber Intelligence Analyst, Strategic Intelligence Analysis
- Bundle

Cyber Warfare
The training explores the evolving landscape of cyber warfare, emphasizing its increasingly complex strategies and challenges.
- Course
- By Treadstone 71

Cyber and Information Operations Leadership Training - In Person
- Course
- By Treadstone 71

Cyber in the Supply Chain
Companies and the DOD have complex supply chains that includes weapons systems and goods.
- Course
- By Treadstone 71

Deception Planning
Cyber Cognitive Warfighter - Denial and Deception
- Course
- By Treadstone 71

Dirty Tricks - Cyber Psyops
CounterIntelligence and Deception - Dirty Tricks used online
- Course
- By Treadstone 71

Disinformation - Cognitive Warfare - Misinformation & Influence Operations
Information Warfare, Types of Disinformation, and Disinformationists
- Course
- By Treadstone 71
Free - Cyber Intelligence Course Overview with a Cyber CounterIntel Sneak Preview
Cyber Intelligence Cert and a sneak preview of Cyber CounterIntel, Cognitive Warfare, and Cyber Intelligence Basics
- Course
- By Treadstone 71
Free - Threat Hunting with TaHiTI and MaGMa
Understanding TaHiTI and using MaGMa
- Course
- By Jeff Bardin
Generative AI - Certified Cyber CounterIntelligence Analyst
Generative AI - Cyber CounterIntelligence Tradecraft - Counter Disinformation, Misinformation while building Cyber CounterIntelligence Plans to Subvert the Adversary
- Course
- By Treadstone 71

Intelligence Requirements
Build your intelligence requirements to effectively address stakeholder needs. Learn the right way, here!
- Course
- By Jeff Bardin

Iranian Cognitive & Information Warfare Section 1 - Cyber Psyops
Grey zone activities, cognitive warfare actions, info warfare, cyber psyops, & primary APTs
- Course
- By Treadstone 71

Iranian Cognitive and Information Warfare Section 2 - Cyber Psyops
Measuring Iran's Cyber Capability with STEMPLES Plus
- Course
- By Treadstone 71

Myers-Briggs Personality Typing - Under Pressure and Destructive Modes
Learn the MBTI and how to understand and influence your adversary personas
- Course
- By Treadstone 71
On Demand - Analytic Writing (Reporting and Briefs)
Learn how to inform quickly with clear, concise, complete, usable, relevant and timely intel
- Course
- By Jeff Bardin
On Demand - Structured Analytic Techniques
Structured analysis is a mechanism by which internal thought processes are externalized systematically and transparently so that they can be shared. We continually enhance existing techniques while adding new options.
- Course
- By Jeff Bardin
On Demand Strategic Intelligence Analysis Plus Building and Enhancing Your CTI Program
Build and Enhance Your CTI Program - Intensive and In-depth Hands-on - 10 Additional Lectures with Templates and Examples - Learn and Build at the same time
- Course
- By Jeff Bardin
On-Demand - Self Paced - Generative AI - Cyber Intelligence Tradecraft - Certified Threat Intelligence Analyst -
On Demand - Cyber Intelligence Tradecraft Cyber Intelligence Training Course Newly extended and updated content with Generative AI
- Course
- By Treadstone 71

Overview of the Global Resilience Federation, Operational Resiliency Framework and CMM.
Guidelines that ensure the continuity and recovery of critical data, systems, and processes.
- Course
- By Treadstone 71

Personas and OPSEC
Ensuring operational security when using personae to passively collect on your targets.
- Course
- By Treadstone 71

Psychological Operations - Cyber Cognitive Warfighter - A NATO View
Cyber psyops - psychological tactics, techniques in the digital realm to influence or manipulate
- Course
- By Treadstone 71

Psychology of the Seven Radicals - Cyber Psyops
Learn how Russians examine adversaries in cyber HUMINT analysis
- Course
- By Treadstone 71

Russian Cognitive and Information Warfare Section 1 - Cyber Psyops
Cognitive and Information Warfare tactics, techniques, and methods from the Russian Perspective
- Course
- By Treadstone 71

Russian Cognitive and Information Warfare Section 2 - Information Alibi - Cyber Psyops
Cognitive and Information Warfare Methods with a focus on their idea of Information Alibi
- Course
- By Treadstone 71

Russian Grey Zone activities, APT Groups - Timelines and Capabilities
A historical overview of Russian advanced persistent threat groups, their capabilities, timeline
- Course
- By Treadstone 71

Russian STEMPLES Plus, Hofstede Principles, and Indicators of Change
A strategic review of Russian STEMPLES Plus their ability to execute offensive cyber operations
- Course
- By Treadstone 71
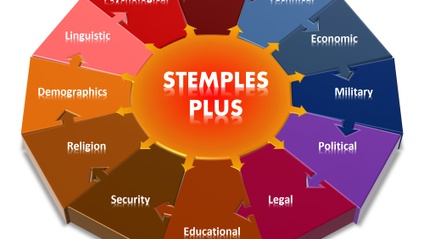
STEMPLES Plus - Indicators of Change - Hofstede Principles
Learn how to assess your adversary strategically with STEMPLES Plus
- Course
- By Treadstone 71

Satellite Cybersecurity
Expanded attack surfaces leads to extend cyber attacks
- Course
- By Treadstone 71

Stakeholder Analysis
How best to understand your leadership and their knowledge of cyber intelligence.
- Course
- By Jeff Bardin

Strategic Source Evaluation - Credibility, Validity, Relevance, and Types of Evidence
The core of your analysis is based on your evidence.
- Course
- By Jeff Bardin

The Big 5 in Cyber Intelligence
What is it? How to recognize traits? Maladaptive modes and manipulation
- Course
- By Treadstone 71

The Dark Triad and Pitch-Black Tetrad
The Dark Triad is made up of three traits: Machiavellianism, Narcissism and Psychopathy. They are considered to be fairly prevalent in the world of work. Researchers have linked these behavioral traits with the process of acquiring of leadership. The dark triad has been found to be particularly highly represented in more senior roles, including the C-suite. In fact, some researchers have put the proportion of CEOs with clinically significant levels of psychopathic traits as high as 20%.. We see the dark triad as incomplete and have added schadenfreude as the fourth area of measurement, representing the Pitch-Black Tetrad.
- Course
- By Treadstone 71